Last week, a security researcher alerted us to an enormous spam list, a colossal 711 million records to be precise. To put this into perspective, while “big” spam lists are not new to Have I Been Pwned (HIBP), with past instances like the River City Media breach containing 393 million records, this “Onliner Spambot” list dwarfs them all. This single data set is so vast it almost equates to an email address for every person in Europe. This article will delve into the details of this unprecedented data exposure.
The discovery was made by Benkow moÊžuÆŽq, a researcher known for his insightful malware and spambot analysis. His previous work, such as the “Spambot safari #2 – Online Mail System” analysis, showcases his expertise in dissecting the mechanics of spam operations and the often-shoddy code behind them. Benkow identified a machine utilized by the “Onliner Spambot” and directed us to an openly accessible directory listing on an IP address:
 Directory Listing of Files
Directory Listing of Files
This image displays a directory listing of files, part of the Onliner Spambot data breach, with sensitive information intentionally obscured to protect the server’s location and prevent further data dissemination.
To safeguard the data and pending law enforcement action, certain details remain obfuscated. The server is located in the Netherlands, and collaborative efforts are underway with law enforcement to shut it down swiftly. Full file names are withheld for now, but relevant details will be discussed.
Before proceeding, it’s crucial to acknowledge Benkow’s detailed analysis of the “Onliner Spambot” mechanics, providing valuable technical context. Zack Whittaker’s report on ZDNet also offers a comprehensive overview of the situation. This article aims to complement these resources by focusing on the exposed data itself, addressing the concerns of individuals who might find their information on HIBP due to this breach and are seeking clarity.
The “Onliner Spambot” data primarily comprises two critical categories:
- Email Addresses: Massive quantities of email addresses solely intended for spam distribution. Some files contain tens to hundreds of millions of addresses.
- Email Addresses and Passwords: These credentials are used to potentially hijack owners’ SMTP servers for spam campaigns. It is also suspected that many are aggregations from previous data breaches.
Personal experience underscores the breadth of this breach. My own email address was found twice within the “Onliner Spambot” data:
A screenshot showing the author’s email address appearing twice within the Onliner Spambot data files, highlighting the widespread nature of the breach.
The file names, like “UK” and “AU,” suggest geographical targeting, but these labels are not entirely accurate. Despite the “UK” suffix, I, not being from the UK, was included. The sheer volume of addresses implies a global reach beyond these initial country codes.
One file, prefixed “NewFile_,” contained over 43,000 entries linked to the Roads and Maritime Services (RMS) of New South Wales, Australia:
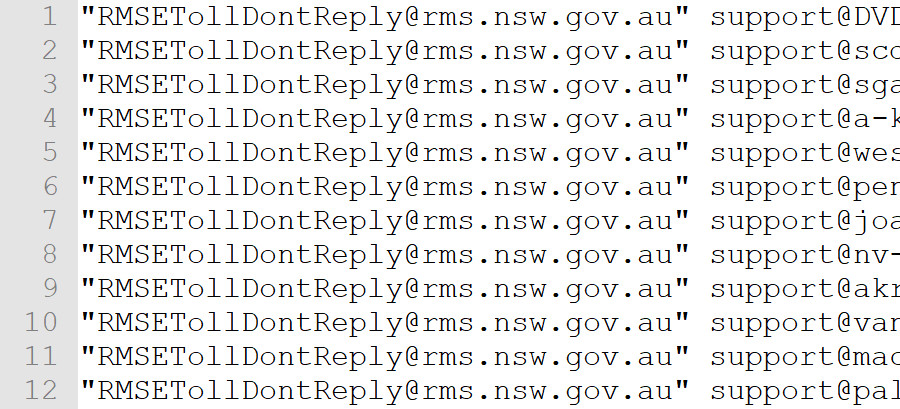 RMS E-Toll
RMS E-Toll
This image shows a sample of data related to RMS E-Toll accounts found within the Onliner Spambot breach, exhibiting a pattern of email addresses associated with toll road services.
Each entry includes [email protected] and “support@” followed by domains, predominantly .com.au but also a significant number of .ru domains. This email is used for Australian toll road notifications. The presence of numerous .ru domains linked to Australian toll accounts is anomalous, suggesting these are not legitimate users. The consistent alias points to auto-generated accounts. This pattern mirrors the B2B USA Businesses spam list, where fabricated addresses were prevalent.
Data quality within the “Onliner Spambot” list varies. Some entries appear to be poorly parsed web scrapes. For instance, this unusual entry was found twice: Employees-bringing-in-their-own-electrical-appliances.htmlmark.cornish@bowelcanceruk.org.uk.
A screenshot illustrating a poorly parsed email address extracted from the Onliner Spambot data, likely scraped from a webpage and improperly formatted.
While partially obscured here, the full address is publicly available in a PDF document. The extraneous “Employees-bringing-in-their-own-electrical-appliances.html” prefix suggests web scraping and flawed parsing. Thus, the “711 million” figure includes some malformed or invalid entries, reducing the actual number of unique, valid email addresses.
Password data is also present. One file contained 1.2 million entries, including password data:
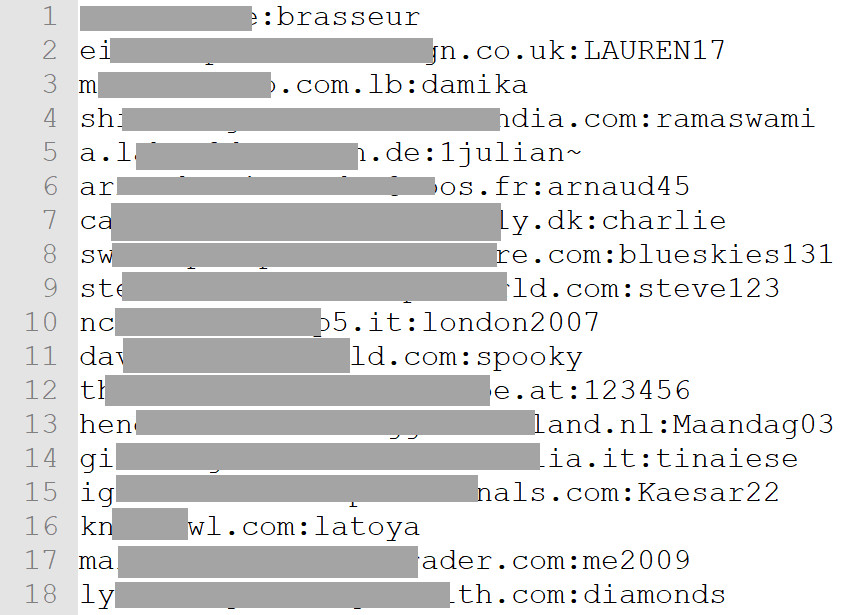 Password file
Password file
This image displays a portion of a password file from the Onliner Spambot breach, containing email addresses alongside associated passwords, potentially compromised credentials.
A spot-check of a dozen addresses revealed every single one was also in the LinkedIn data breach. These passwords were originally exposed as unsalted SHA1 hashes, making them easily crackable. This suggests the “Onliner Spambot” list reuses data from previous breaches.
Another file contained 4.2 million email and password pairs, all linked to the Exploit.In combo list. This illustrates the cyclical nature of data breaches; once exposed, data is repeatedly repackaged and redistributed.
Further files reveal even larger datasets. One with 29 million entries of email and password combinations showed consistent hits in HIBP, though without a clear single source breach. Another, seemingly targeting Australia, contained 12.5 million records, a significant portion not found in HIBP, including 379,000 .gov.au addresses – a mix of valid, fake, and malformed entries.
Crucially, some files include SMTP server and port details, like this example with over 3,000 records:
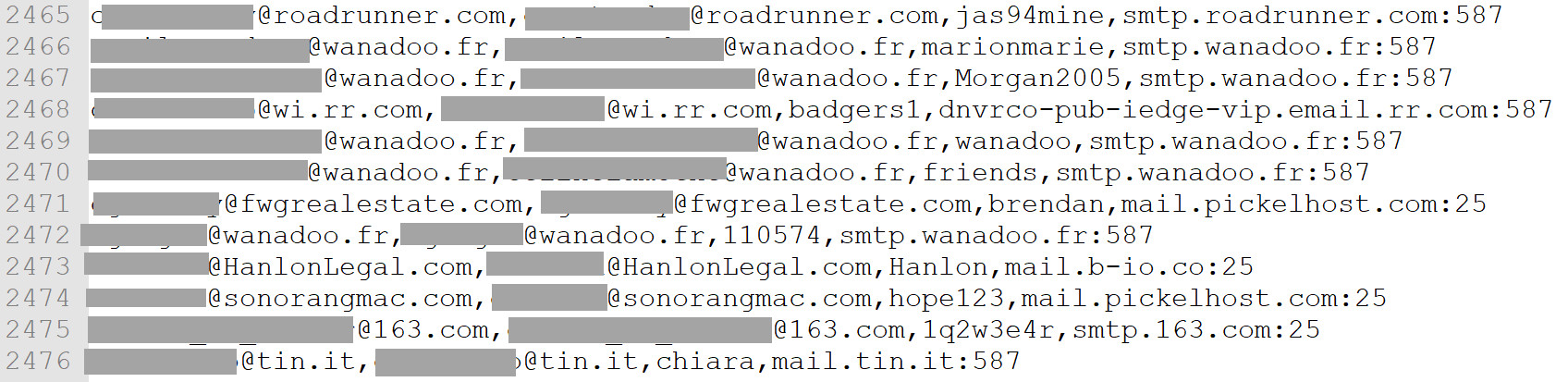 SMTP data
SMTP data
An example of SMTP data extracted from the Onliner Spambot files, showing email addresses paired with SMTP server and port information, valuable for spammers to send emails.
This SMTP data is highly valuable for spammers, providing access to legitimate mail servers for sending spam. Another file contained 142,000 such records.
Some data is unstructured. A file with 20 million Russian email addresses was intermixed with what appeared to be SQL file names:
 Russian-data
Russian-data
This image shows a segment of Russian email addresses mixed with SQL file names, indicating a diverse range of data sources within the Onliner Spambot collection.
In summary, the “Onliner Spambot” data encompasses email addresses, passwords, and SMTP details across gigabytes of files. The sheer scale is staggering. HIBP accumulated 711 million records over 2.5 years across 110 breaches; this single “Onliner Spambot” incident matches that volume.
The examples are not exhaustive but illustrate the data’s diversity and explain why some entries are invalid. Finding your address in this “Onliner Spambot” list doesn’t pinpoint the original breach source or offer direct remediation steps. Even for someone deeply involved in data breach analysis, like myself, finding my email in this list was a stark reminder of the pervasive nature of spam. Our email addresses are commodities, traded and exploited to bombard us with unwanted solicitations. This is the current reality of the internet.
All 711 million records from the “Onliner Spambot” are now integrated and searchable on HIBP.
Addressing Common Questions:
Regarding password availability on HIBP, passwords are not made publicly available. Displaying passwords poses significant security risks.
Providing indicators of password presence for each email address is also challenging due to:
- Messy Source Data: Parsing the unstructured data to reliably extract password flags would be extremely complex.
- Password Requests: Even indicating password presence would lead to password requests, which is against HIBP’s security principles.
- Data Breach Attribute Variety: Data breaches contain diverse data types. Indicating every attribute for every record is impractical.
- HIBP Feature Limitations: The current HIBP architecture doesn’t support this level of granular attribute detail.
What to Do Now:
Your response depends on your current security practices:
- Password Manager Users: If you use a password manager with strong, unique passwords, you are likely at low risk. The “Onliner Spambot” data originates from older breaches like LinkedIn with hashed passwords. Even unsalted SHA1 hashes are still robust against cracking for long, random passwords. Passwords observed in the data were generally weak.
- Non-Password Manager Users: Start using a password manager immediately. Your weak passwords are likely compromised and have been for some time. Implement a password manager like 1Password and prioritize changing passwords for critical accounts first, then others over time.
Regardless of your current situation, enable multi-factor authentication (MFA) everywhere possible. MFA renders stolen credentials useless, even if passwords are exposed.
These steps require minimal effort but significantly enhance your security posture.
